Is Your Payment Data Secure? Why PCI DSS Matters.

When it comes to payment gateways, PCI DSS (Payment Card Industry Data Security Standards) really matter, and not all payment gateways are made equally. Apriva’s PCI DSS and PCI P2PE Certified payment gateway provides the highest possible level of payment data security to merchants. Here’s how.
At its core, Apriva operates a payment gateway service, serving a variety of merchants. This gateway supports a variety of products, from vending and self-service payment enablement to our AprivaPay Any Way suite. In the world of business compliance, and handling people’s sensitive transaction information, Apriva recognizes its inherent responsibility to deliver the most secure products possible to its customers. Security and compliance should always be considered critical traits for any service or product operating in the financial space, but Apriva strives to take it a step further.
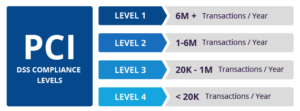
Apriva is considered a Level 1 Service Provider. To qualify as level 1, service providers have to store, process, and transmit more than 300,000 credit card transactions annually (we exceed this by over 439% every year), as well as meet validated PCI DSS and PCI P2PE requirements. We’ll talk more about those in a moment. Beyond that, Apriva is required to advertise the status of its assessment with Visa, at https://www.visa.com/splisting/searchGrsp.do.
But here’s the deal. Everyone that offers a payment gateway talks about security, and promises that they have the best. The reality is Apriva is one of the only PCI DSS P2PE Certified Payment Gateways serving the payment industry in the United States. Period. Some may claim P2PE, but they are “self-assessed”. Apriva is certified by a PCI Council approved auditor every 2 years, on top of an internal audit performed every year against the exacting guidelines of the PCI Council. What this means is cardholder data is encrypted/encoded in the highest level of security from the moment the consumer presents their credit card until it is delivered to the credit card processor. The odds of you being responsible for a data breach are as low as they possibly can be, thanks to Apriva’s technology.
The reality is, your reputation is on the line when you accept consumer credit card data. Other providers may claim “don’t worry, we’re the merchant of record, we take responsibility for a data breach”. But in reality, if a data breach happens to a merchant, the public doesn’t care – your name will be held responsible, not your merchant of record.
Here’s a little more information about payment gateways and the PCI DSS, if you want to learn more.
How does a payment gateway work?
Once a customer swipes, dips, or taps their payment information, it is encrypted and securely passed to the payment gateway. The most secure way to do this is through P2PE or Point-to-point encryption, which is what Apriva’s gateway uses. The Payment gateway then encrypts the card details and runs a security check on the encryption before passing the information along to the customers’ acquiring bank (an acquiring bank is the bank on the merchants’ end of the transaction). The acquiring bank then sends the information securely to the card brand (i.e. Visa, Mastercard, etc.). The card brand then ensures another layer of security before sending the information to the issuing bank (the issuing bank is the cardholder or consumer’s bank), who then authorizes (or denies) the transaction. The approved or denied message is then sent back to the card brand, back to the acquiring bank, back to the payment gateway, and then back to the merchant, who can then collect payment. This entire process takes less than 3 seconds to complete on average, but is vital to protecting and securing sensitive payment data.
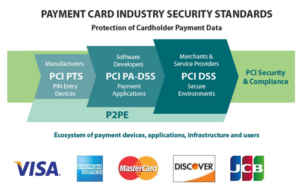
Payment Card Industry Security Standards Council (PCI SSC)
In addition to internally developed security standards, there are also commonly accepted industry standards and regulations that apply to the services Apriva provides its customers. One common set of requirements in the payments industry is established by the payment card brands (American Express, Discover, JCB International, Mastercard and Visa Inc). That set of requirements is maintained by an organization called the Payment Card Industry Security Standards Council (PCI SSC).
PCI DSS
The PCI SSC has established a standard called the Data Security Standard (PCI DSS). Every year, Apriva’s Payment Gateway and associated services are audited by an unbiased third-party. The audit covers 12 security categories and objectives with over 400 individual security and compliance controls. A successful evaluation of service delivery is required for the PCI DSS certification. The certification is required to be registered with the Visa Global Registry of Service Providers.
P2PE
In some business cases, the payments industry requires even more strict controls to be in place. One example of this would be the Apriva P2PE Solution. When a device such as a made-for-purpose POS terminal runs a credit card transaction, it collects data associated with the credit card. The data collected is referred to as Card Holder Data (CHD) and, if data is collected via swiped transaction, it includes what is referred to as ‘track’ data. P2PE approved devices operate in similar fashion but the difference being that the Apriva P2PE solution requires that customers use the specific devices detailed within the P2PE Instruction Manual (PIM). Apriva provides assurance of additional protections being in place to ensure data security that is maintained according to the P2PE standards outlined.
With Apriva as your business partner, you can rest assured knowing that the data provided by your customers is treated with the security and integrity it deserves. Apriva’s P2PE solution ensures the security of the network, the card readers, the encryption keys, data storage and transmission, and a litany of technological attack vectors that you wouldn’t be expected to think about. Apriva has taken that extra step for you by obtaining the certification.
- Evaluation of key management and password strength controls
- Use of certified key injection facilities (KIFs)
- Validation that the PTS approved POI devices have not been tampered with
- Validation that the device received is correctly identified, evaluated, emplaced, and functions as expected
Data Matters: The C.I.A. of Data Protection
Information Security and Compliance teams serve the primary purpose of protecting data. But what does that mean, really? Data protection falls into three (3) categories of control:
- Confidentiality
- Integrity
- Availability
When you hear about the latest ‘data leaks’ or ‘hacks’, regardless of how the attack has been performed and who is doing it, the outcome involves a desire to gain access to, compromise the integrity of, or make unavailable, customer’s data. It stands to reason that Apriva be focused on mitigating those risks through well-defined, industry accepted methods and practices. To assist in defining an attack landscape, Security and Compliance professionals throughout the organization use a variety of tools and resources in concert to provide both automation and real-time, eyes-on, oversite of systems that transmit, receive, and store your data.
Apriva has taken the time to look at each step in the process of handling your data to ensure it is properly encrypted or otherwise protected at the point-of-interaction (think card swipe/dip), during the time it’s on the public internet (data-in-transit), and wherever the data is stored (data-at-rest). To these ends, Apriva uses both data encryption and tokenization techniques to minimize the risks associated with a data leak or hack.
What is ‘encryption’?
Encryption is a means by which message data is scrambled so that only the intended recipient is able to recover the message provided. The means by which the message is scrambled can be something simple (e.g. a substitution cipher that shifts characters by three positions whereby A = D, B = E, C = F, and so on). Modern encryption is significantly more complex and varied in terms of how it can be implemented. Simply stated, mathematic equations are applied to the original data to ensure that A) the new data set is unreadable and B) the new data set can be opened by the intended recipient only as long as the intended recipient has the proper key to unlock the message.
Part of our job at Apriva is to ensure that only strong encryption methodologies are used to protect you and your customer’s data. As you might imagine, the definition of ‘strong encryption’ changes over time. We strive to keep it simple for our customers by regularly evaluating technology trends in data protection practices. Apriva is committed to keeping up with the latest security threats and risks, and takes the steps to mitigate those risks on an on-going basis.
What is ‘tokenization’?
Tokenization is the means by which sensitive data (there are many definitions of sensitive data and that’s worth discussing later) into non-sensitive data (a.k.a. a ‘token’). The token can then be transferred among consumers who might need access to the original data and allows the approved consumers the ability to access the original sensitive data. Simply put, a token is a piece of data that stands in for another piece of data. The token itself has no intrinsic value (think ‘poker chip’ versus gold or cash). The valuable data is retained in a secure database and only accessed when authorized by virtue of a proper token being made available (customer->poker chip -> cashier-> cash -> customer).